As we continue to connect everything to the Internet, we continue to find authentication challenges. VoIP phones, smart TVs, AI-powered webcams, smart HVAC controls, AI-enhanced motion sensors are just some of the IoT devices you may have connected to the network in your office. Behind the scenes you are using systems that are integrated with a range of different API methods (e.g. REST, SOAP, GraphQL.) All of these non-human assets should be authenticated to guard against rogue devices on your network, but not even your authorized devices will all work with whatever authentication systems you have. It is a complex mess to try and wrangle.
For your users you diligently implemented a central directory to authenticate users (probably Microsoft Active Directory or Entra ID.) Then you added something for multifactor authentication because it is a dangerous World out there. Some of your users still log in to other directories for specific purposes or applications that don’t integrate with your primary one. In the course of a regular day, your users are entering (hopefully) different credentials into different systems all with different interfaces. As we add user behaviour analytics to our security controls, it appears to users that we are randomly prompting them for credentials again. We haven’t made it easy for the users. But they are trained to enter credentials when prompted because “it keeps things secure.”
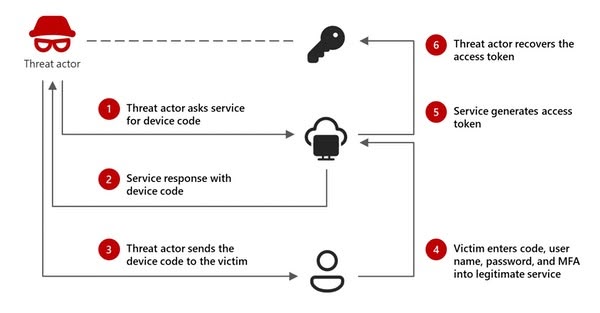
The threat actors have found a novel way to take advantage of the cracks in the modern business environment — the smart TVs! Not directly through the TVs themselves, but taking advantage of the simplified authentication method created for these devices and applying tried and true phishing techniques. The linked article has a good explanation of the process if you want the details.
Technology integration has always been a bumpy evolution. There are periods of sprawl where different systems require different protocols and IT struggles to manage the complexity. This is followed by a period of consolidation where the number of systems are reduced and the remaining ones are configured on standards. This is inherently limiting. Eventually business demands push exceptions and the period of non-standard sprawl begins again.
Anything “smart”, “AI”, or “IoT” is not yet standardized. The period of complex sprawl is well underway again. This time though, the users aren’t just users of the systems, they are “implementing” systems (cloud SaaS) and we expect them to participate in securing systems (use authentication methods properly, be wary of suspicious messages.) We used to try and hide IT complexity from users, but if we are going to rely on them to help manage the technology, we need to give them the tools and knowledge to do it effectively.
https://www.tripwire.com/state-of-security/microsoft-teams-storm-2372-exploit-device-codes